isco ASA 5500 Series appliances deliver IPsec and SSL VPN, firewall, and several other networking services on a single platform. Cisco ASA 5520, a member of the Cisco ASA 5500 Series, is shown in Figure 1 below.

Figure 1 Cisco Adaptive Security Appliance (ASA)
In this article, we will focus on site-to-site IPsec implementation between two Cisco ASA 5520 appliances, as shown in Figure 2. The outside interface of ASA1 is assigned a dynamic IP addressby the service provider over DHCP, while the outside interface of ASA2 is configured with astatic IP address. Basic IP address configuration and connectivity exists and we will build IPsec configuration on top of this. Although this tutorial was tested on ASA5520, the configuration commands are exactly the same for the other ASA models with no difference.
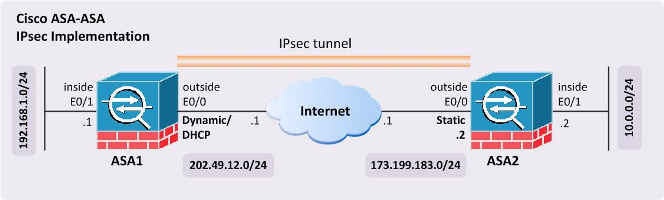
Figure 2 Cisco ASA-ASA IPsec Implementation
IP Security (IPsec) can use Internet Key Exchange (IKE) for key management and tunnel negotiation. IKE involves a combination of ISAKMP/Phase 1 and IPsec/Phase 2 attributes that are negotiated between peers. If any one of the attributes is misconfigured, the IPsec tunnel fails to establish. Therefore, it is mandatory to make sure that all these parameters are identical on the two appliances we are using as IPsec peers.
We will start with a preconfiguration checklist to make our life easier. This checklist would serve as a reference for configuration and troubleshooting.
Table 1 Configuration Checklist: ISAKMP/Phase-1 Attributes
| Attribute | Value |
| Encryption | AES 128-bit |
| Hashing | SHA-1 |
| Authentication method | Preshared keys |
| DH group | Group 2 1024-bit field |
| Lifetime | 86,400 seconds |
After discussing Phase 1 attributes, it is important to highlight Phase 2 attributes of the IPsec VPN connection, that are used to encrypt and decrypt the actual data traffic.
Table 2 Configuration Checklist: IPsec/Phase-2 Attributes
| Attribute | Value |
| Encryption | AES 128-bit |
| Hashing | SHA-1 |
| Lifetime | 28,800 seconds4,608,000 kB |
| Mode | Tunnel |
| PFS group | None |
Now that we have determined what Phase 1 and Phase 2 attributes to use, we’re ready to configure the site-to-site IPsec tunnel between ASA1 and ASA2.
Let’s start with configuring ASA1:
! ISAKMP Phase 1
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
crypto ikev1 enable outside
tunnel-group 173.199.183.2 type ipsec-l2l
tunnel-group 173.199.183.2 ipsec-attributes
ikev1 pre-shared-key Cisc0
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
crypto ikev1 enable outside
tunnel-group 173.199.183.2 type ipsec-l2l
tunnel-group 173.199.183.2 ipsec-attributes
ikev1 pre-shared-key Cisc0
! IPsec Phase 2
access-list RED permit ip 192.168.1.0 255.255.255.0 10.0.0.0 255.255.255.0
crypto ipsec ikev1 transform-set ESP-AES128-SHA esp-aes esp-sha-hmac
crypto map VPN-MAP 10 match address RED
crypto map VPN-MAP 10 set peer 173.199.183.2
crypto map VPN-MAP 10 set ikev1 transform-set ESP-AES128-SHA
crypto map VPN-MAP interface outside
crypto ipsec ikev1 transform-set ESP-AES128-SHA esp-aes esp-sha-hmac
crypto map VPN-MAP 10 match address RED
crypto map VPN-MAP 10 set peer 173.199.183.2
crypto map VPN-MAP 10 set ikev1 transform-set ESP-AES128-SHA
crypto map VPN-MAP interface outside
Here goes the configuration for ASA2:
! Create ISAKMP policy
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 enable outside
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 enable outside
! Define the pre-shared key within the dynamic map tunnel group
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key Cisc0
!
crypto ipsec ikev1 transform-set ESP-AES128-SHA esp-aes esp-sha-hmac
ikev1 pre-shared-key Cisc0
!
crypto ipsec ikev1 transform-set ESP-AES128-SHA esp-aes esp-sha-hmac
access-list BLUE permit ip 10.0.0.0 255.255.255.0 192.168.1.0 255.255.255.0
! Create a dynamic-map
crypto dynamic-map DYN-MAP 20 match address BLUE (OPTIONAL)
crypto dynamic-map DYN-MAP 20 set ikev1 transform-set ESP-AES128-SHA
crypto dynamic-map DYN-MAP 20 set ikev1 transform-set ESP-AES128-SHA
! Assign the dynamic-map to crypto map
crypto map VPN-MAP 10 ipsec-isakmp dynamic DYN-MAP
crypto map VPN-MAP interface outside
crypto map VPN-MAP interface outside
The above commands conclude the IPSEC VPN configuration. However, if we have NAT in our network (which is true most of the times), we still have some way to go. We must configure NAT exemption for VPN traffic. That is, traffic that will pass through the VPN tunnel (i.e traffic between the LAN networks 192.168.1.0/24 10.0.0.0/24) must be excluded from NAT operation.
Configure NAT Exemption on ASA1
ASA1(config)# object network obj-local
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# exit
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# exit
ASA1(config)# object network obj-remote
ASA1(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA1(config-network-object)# exit
ASA1(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA1(config-network-object)# exit
ASA1(config)# object network internal-lan
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# exit
ASA1(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA1(config-network-object)# exit
! Exclude traffic from LAN1 to LAN2 from NAT operation
ASA1(config)# nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
! Configure Port Address Translation (PAT) using the outside ASA interface. This will perform dynamic NAT on internal LAN hosts so that they can access the Internet.
ASA1(config)# object network internal-lan
ASA1(config-network-object)# nat (inside,outside) dynamic interface
ASA1(config-network-object)# nat (inside,outside) dynamic interface
Configure NAT Exemption on ASA2
ASA2(config)# object network obj-local
ASA2(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA2(config-network-object)# exit
ASA2(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA2(config-network-object)# exit
ASA2(config)# object network obj-remote
ASA2(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA2(config-network-object)# exit
ASA2(config-network-object)# subnet 192.168.1.0 255.255.255.0
ASA2(config-network-object)# exit
ASA2(config)# object network internal-lan
ASA2(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA2(config-network-object)# exit
ASA2(config-network-object)# subnet 10.0.0.0 255.255.255.0
ASA2(config-network-object)# exit
! Exclude traffic from LAN2 to LAN1 from NAT operation
ASA2(config)# nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
! Configure Port Address Translation (PAT) using the outside ASA interface. This will perform dynamic NAT on internal LAN hosts so that they can access the Internet.
ASA2(config)# object network internal-lan
ASA2(config-network-object)# nat (inside,outside) dynamic interface
ASA2(config-network-object)# nat (inside,outside) dynamic interface
At this point our IPsec configuration is complete. We can generate some traffic from a host in subnet 192.168.1.0/24 connected to ASA1 to a host in subnet 10.0.0.0/24 connected to ASA2. An easy way to generate such traffic is the good old ping utility. If ping is successful between the two subnets, an IPsec tunnel is also likely to have established successfully. The same can be verified using command show crypto ipsec stats:
ASA1# show crypto ipsec stats
IPsec Global Statistics
———————–
Active tunnels: 1
Previous tunnels: 1
Inbound
Bytes: 400
Decompressed bytes: 400
Packets: 4
Dropped packets: 0
Replay failures: 0
Authentications: 4
Authentication failures: 0
Decryptions: 4
Decryption failures: 0
Decapsulated fragments needing reassembly: 0
———————–
Active tunnels: 1
Previous tunnels: 1
Inbound
Bytes: 400
Decompressed bytes: 400
Packets: 4
Dropped packets: 0
Replay failures: 0
Authentications: 4
Authentication failures: 0
Decryptions: 4
Decryption failures: 0
Decapsulated fragments needing reassembly: 0
Outbound
Bytes: 400
Uncompressed bytes: 400
Packets: 4
Dropped packets: 0
Authentications: 4
Authentication failures: 0
Encryptions: 4
Encryption failures: 0
Fragmentation successes: 0
Pre-fragmentation successses: 0
Post-fragmentation successes: 0
Fragmentation failures: 0
Pre-fragmentation failures: 0
Post-fragmentation failures: 0
Fragments created: 0
PMTUs sent: 0
PMTUs rcvd: 0
Protocol failures: 0
Missing SA failures: 0
System capacity failures: 0
Bytes: 400
Uncompressed bytes: 400
Packets: 4
Dropped packets: 0
Authentications: 4
Authentication failures: 0
Encryptions: 4
Encryption failures: 0
Fragmentation successes: 0
Pre-fragmentation successses: 0
Post-fragmentation successes: 0
Fragmentation failures: 0
Pre-fragmentation failures: 0
Post-fragmentation failures: 0
Fragments created: 0
PMTUs sent: 0
PMTUs rcvd: 0
Protocol failures: 0
Missing SA failures: 0
System capacity failures: 0
You can get your hands dirty with several other show crypto commands available to verify configuration and view statistics. For example, show crypto isakmp sa detail command can be used to verify ISAKMP/Phase 1 attributes, while show crypto ipsec sa command can be used to verify IPsec/Phase 2 attributes. We have shown here the output for show crypto isakmp sa detailcommand:
ASA1# show crypto isakmp sa detail
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 173.199.183.2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Encrypt : aes Hash : SHA
Auth : preshared Lifetime: 86400
Lifetime Remaining: 85998
Rekey : no State : MM_ACTIVE
Encrypt : aes Hash : SHA
Auth : preshared Lifetime: 86400
Lifetime Remaining: 85998
I am sure this paragraph has touched all the internet
ReplyDeleteviewers, its really really pleasant post on building up new webpage.
Blog Commenting Sites
social bookmarking sites list
dofollow social bookmarking sites
web 2.0 sites
browser list
The post is written in very a good manner and it contains many useful information for me. windscribe free
ReplyDeleteGood post but I was wondering if you could write a litte more on this subject? I’d be very thankful if you could elaborate a little bit further. Appreciate it! tor vs vpn
ReplyDeleteNew web site is looking good. Thanks for the great effort. avast vpn torrenting
ReplyDelete