In this article we will see a site-to-site VPN using the IPSEC protocol between a Cisco ASA and a pfSense firewall. PfSense is an open source distribution of FreeBSD customized for use as a firewall and router. You can install pfSense on a PC with two (or more) NICs, essentially turning it into a flexible security appliance. You can obtain your copy of pfSense from the Downloads section of www.pfsense.org. At the time of this writing, the latest available release is 2.0.2 and the same has been used in this tutorial.
In this article, we will focus on site-to-site IPsec implementation between a Cisco ASA and a pfSense firewall, as shown in Figure 1 below.
Figure 1 Cisco ASA to pfSense IPsec Implementation (Click for Larger Picture)
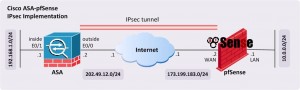
Table 1 Preconfiguration Checklist: ISAKMP/Phase-1 Attributes
| Attribute | Value |
| Encryption | AES 128-bit |
| Hashing | SHA-1 |
| Authentication method | Preshared keys |
| DH group | Group 2 1024-bit field |
| Lifetime | 86,400 seconds |
Table 2 Preconfiguration Checklist: IPsec/Phase-2 Attributes
| Attribute | Value |
| Encryption | AES 128-bit |
| Hashing | SHA-1 |
| Lifetime | 28,800 seconds4,608,000 kB |
| Mode | Tunnel |
| PFS group | None |
ASA Configuration
Let’s start with configuring the ASA (Using ASA 8.4(2) in this example):
! IPsec ISAKMP Phase 1
crypto ikev1 policy 1! IPsec Phase 2
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
exit
!
crypto ikev1 enable outside
tunnel-group 173.199.183.2 type ipsec-l2l
tunnel-group 173.199.183.2 ipsec-attributes
ikev1 pre-shared-key Cisc0
crypto ipsec ikev1 transform-set pfSense-AES128SHA esp-aes esp-sha-hmacPfSense Configuration
!
access-list outside_cryptomap_10 remark ACL to encrypt traffic from ASA to pfSense
access-list outside_cryptomap_10 extended permit ip 192.168.1.0 255.255.255.0 10.0.0.0 255.255.255.0
!
crypto map outside_map 10 match address outside_cryptomap_10
crypto map outside_map 10 set peer 173.199.183.2
crypto map outside_map 10 set ikev1 transform-set pfSense-AES128SHA
crypto map outside_map interface outside
We open the URL http://173.199.183.2 in a Web browser to access the pfSense firewall and enter the default username/password of admin/pfsense. You may have noticed that 173.199.183.2 is the WAN IP address of the pfSense firewall that indicates we are accessing it from the Internet.

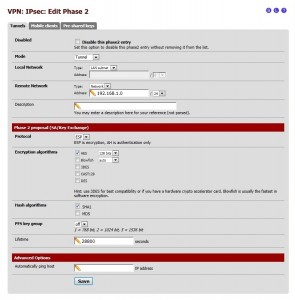
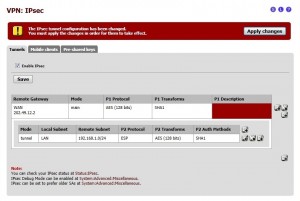
In order to check IPsec tunnel status on the pfSense firewall, go to Status > IPsec. If you see a tiny green icon in the Status column, IPsec tunnel is successfully established as shown in the following screenshot.

Hi,
ReplyDeleteCould you change the screenshots, they are too small.
Thank you
Cool manual.Thank you.
ReplyDeletetop10-bestvpn.com
Good manual for VPN connection.It works fine.Thanks for configuration and scripts.
ReplyDelete10webhostingservice.com
AirVPN.org and mullvad.net deserve some props. They are awesome and accept bitcoin as well. With 3 tunnels per account, I think mullvad is by far the best deal around.
ReplyDeleteRegards
Ashley Jones
Deepwebsiteslinks.com
Can you tell me the status of VyprVPN in China at this moment (assuming you are still using VyprVPN)? I ask this because I read that some VPNs may be good today but may not be good tomorrow. So I presume I can get the most updated info from you. I’m traveling to China next week and just need some “assurance” before I commit to VyprVPN. Thanks!
ReplyDeleteBest VPN
Best Dark net markets
Proxy top lists help, but they can be blocked as regular proxy websites as soon as they become famous. I think E-mail lists and search engines are the only ways to get new proxies. They just can’t block e-mail an google 🙂
ReplyDeletechallenges to do with friends
album downloader
Games to play over text
good morning
online grammar checker
Music Download Sites to download legally
newlywed game questions
Reasons why I love you
Hello, i think that i saw you visited my blog thus i came to “return the favor”.I’m attempting to find things to enhance my website!I suppose its ok to use some of your ideas!random email generator
ReplyDeletedirectory submission list